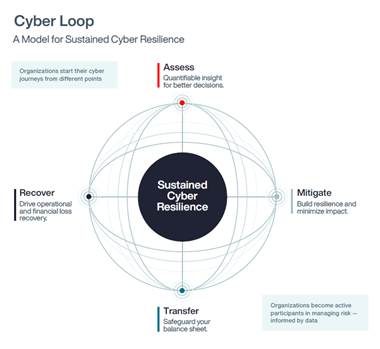
There is nothing linear about cyber security. This is the guiding principle of The Cyber Loop, a cyber risk management model for sustained cyber resilience that unites stakeholders irrespective of role to make better decisions on cyber risk.
According to Aon’s 2021 Cyber Risk Report, business and information technology (IT) leaders are under increasing pressure to maximise return on security investment (ROSI) in an increasingly complex business and risk environment. Insurance providers also feel the pressure. As loss frequency and severity outpace cyber rate increase,[1] and many have halved the amount of cyber coverage they provide to customers after a surge in ransomware attacks left them hurting from considerable payouts.[2] There is no doubt that cyber risk runs deep and wide.
Businesses find themselves ill-prepared to manage this risk. Only two in five organisations are ready to navigate new exposures arising from rapid digital evolution, and more alarming, a mere 17 percent have adequate application security measures in place.[3]
The market continues to overflow with technologies designed to secure organisations and operational checklists to guide compliance and build resilience. Yet even with all these resources, many likely feel unsure of the best next decision. A strategic approach to cyber security is circular and iterative, and importantly — informed by data.
Realising Sustained Cyber Resilience
The Cyber Loop model acknowledges that each organisation will start its journey from a different place: assess, mitigate, transfer, or recover.
This journey through assess, mitigate, transfer, and recover demonstrates that a strategic approach to cyber resilience is circular and iterative, and importantly — informed by data.
When operating within the Cyber Loop, an organisation becomes an informed participant in managing risk. To realise the promise of sustained cyber resilience, it is critical that stakeholders — across the business — come together to assess where they sit in the circular journey. With data, better decisions can be made and return on security investment can be measured.
At the conclusion of each section, key questions are presented to help guide understanding of the value unlocked within each Cyber Loop entry point. Additionally, we provide eight key actions an organisation can take today, to reinforce its cyber security strategy.
Eight actions your organisation can take to today to reinforce its cyber security strategy:
1.Review business continuity and disaster recovery plans to ensure they take account of, and regularly test for, cyber threats.
2. Assess vulnerabilities. This allows the organisation to strategically budget for and address critical areas.
3. Review governance, controls, roles and responsibilities and develop protective safeguards to prevent ransomware attacks.
4. Quantify the financial loss associated with an incident, breach or disruption.
5. Engage in breach simulations and tabletop exercises to test incident preparedness.
6. Check contractual protections and have all insurance policies reviewed to ensure the organisation is covered for financial loss from a breach.
7. Proactively utilise threat intelligence to monitor for the tactics, techniques and procedures of cyber attackers.
8. Never stop cycling through the cyber loop.